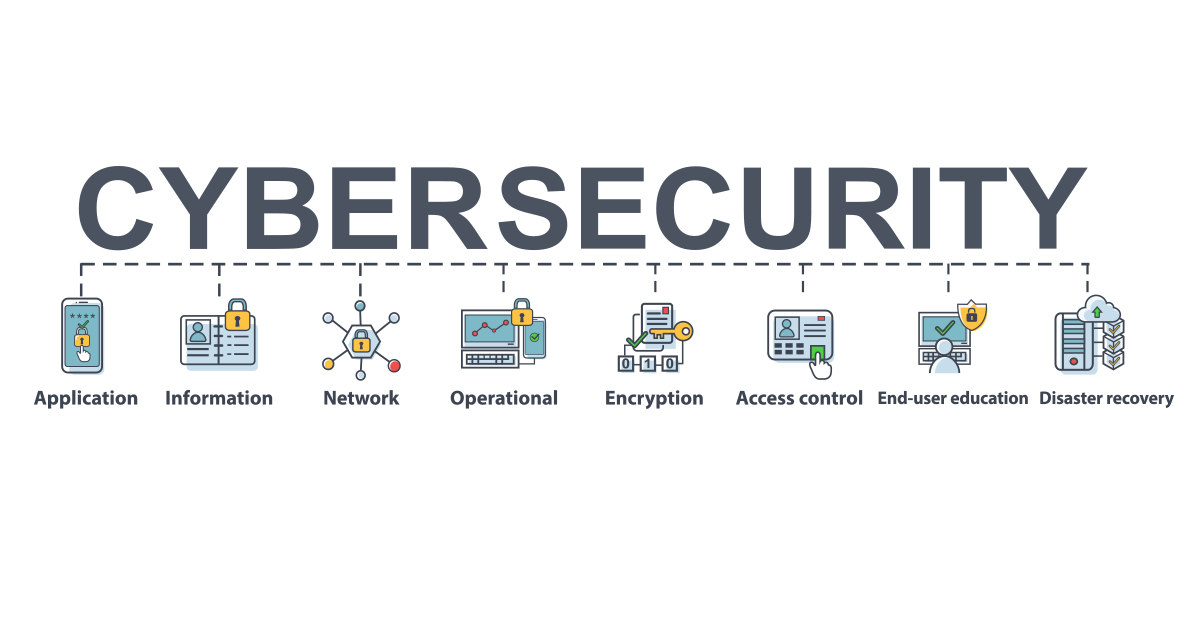
Technology is a major factor in our lives, from personal communication through financial transactions to the rest of our lives security, the significance of cybersecurity can’t be understated. Cybersecurity serves as the digital security shield that protects our private information from spies roaming over the huge expanses of internet. Cyber threats are growing in terms of sophistication and frequency, individuals, businesses, and even governments should prioritize cybersecurity methods to safeguard the integrity as well as the security, confidentiality and accessibility of data.
The digital landscape is rife with cyber-attacks of all kinds, that range from phishing and malware attacks, to ransomware and data breach. Criminals constantly exploit weaknesses within networks, software and human behavior to gain an unauthorised access to sensitive data or disrupt vital services. They not only present substantial financial risk, but they could also threaten security of the nation, privacy as well as public security. As such, the need for a strong cybersecurity strategy in order to stop these attacks has never been more critical.
One of the fundamental pillars of cybersecurity is proactive risk management. The organizations must conduct comprehensive risk assessments to identify potential vulnerabilities and prioritize areas to strengthen. This includes evaluating the security status of the systems, networks and apps, as well as assessing the efficacy of current security controls. In assessing their risk exposure and assessing their vulnerability, companies can take specific security measures that will reduce threats and minimize the likelihood for successful cyber attacks.
The growth of Internet of Things (IoT) devices adds to the complexity of the world. These interconnected devices, ranging from smart appliances for homes to industrial sensors, create new points of entry for cyber criminals. They are often characterized by inadequate security measures and vulnerabilities, IoT devices can be targeted to launch massive cyber attacks as well as botnets or make it difficult to protect your security. Since the quantity of IoT devices continues to soar and increase, the challenge of security they pose becomes increasingly urgent and demands robust security guidelines, regular updates, and increased awareness among users. To generate extra information kindly look at https://www.cyber4you.it/63/protezione-con-centrale-operativa-soc
As the digital landscape changes in the digital age, so do the regulation rules that regulate cybersecurity. The governments of the world are increasingly adopting laws and regulations that aim to improve cybersecurity standards as well as holding businesses accountable for protecting sensitive information. In compliance with the specific industry regulations like GDPR (General Data Protection Regulation) and HIPAA (Health Insurance Access and Accountability Act) does more than reduce the legal risk, but also builds trust between stakeholders and customers. In addition, it facilitates the implementing of robust cybersecurity methods and helps to establish a culture of cybersecurity within organizations.
In the end, cybersecurity is a complex field that requires a complete and proactive approach to reduce any threats to the cyberspace. By employing robust encryption techniques as well as fostering a culture that is cybersecurity and collaboration among stakeholders, organizations are able to better defend themselves from cyber threats and safeguard the integrity, confidentiality, and security of its digital asset. In an era where the stakes have never been higher spending money on cybersecurity is not only an advisable business move and is vital to ensure security, trust, and security in the current digital world.